Enable Cloud Kerberos Ticket Retrieval for AAD joined devices
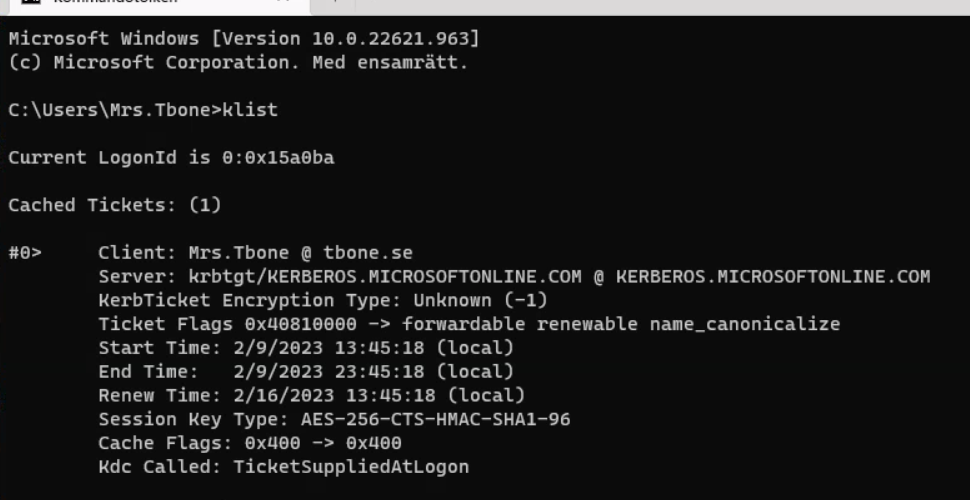
In my previous blog, I went through the simple steps to enable Azure AD Kerberos. This prepares for Azure AD Kerberos Cloud Trust. But when I logged in to a Windows 365 computer with Windows 11 and run klist in CMD. I noticed that there were no Kerberos Ticket Granting Ticket created:
By default the Azure AD Kerberos Ticket Granting Ticket is not retrieved during logon. To configure clients to retrieve a Kerberos ticket at logon, you need to configure the CSP setting CloudKerberosTicketRetrievalEnabled. This can be done easy by deploying this setting with Intune.
Enable Cloud Kerberos Ticket Retrieval in Windows Device
- Open Intune Portal
- Select Devices / Windows / Configuration profiles
- Click Create Profile
- Platform: Windows 10 and later
- Profile type: Templates
- Template name: Custom
- Enter a suitable Name and Description and click Next
- On the Configuration settings, click Add
- Enter the following settings:
- Name: Cloud Kerberos Ticket Retrieval Enabled
- Description: Cloud Kerberos Ticket Retrieval Enabled
- OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Kerberos/CloudKerberosTicketRetrievalEnabled
- Data type: Integer
- Value: 1
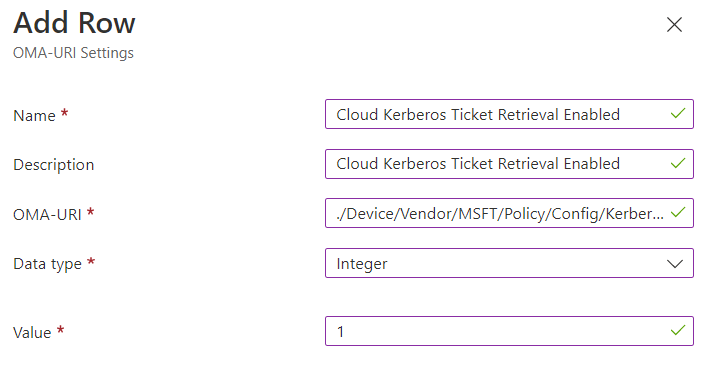
- Save your configuration
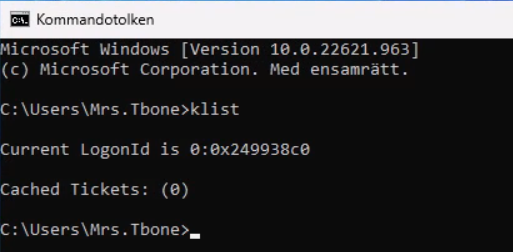
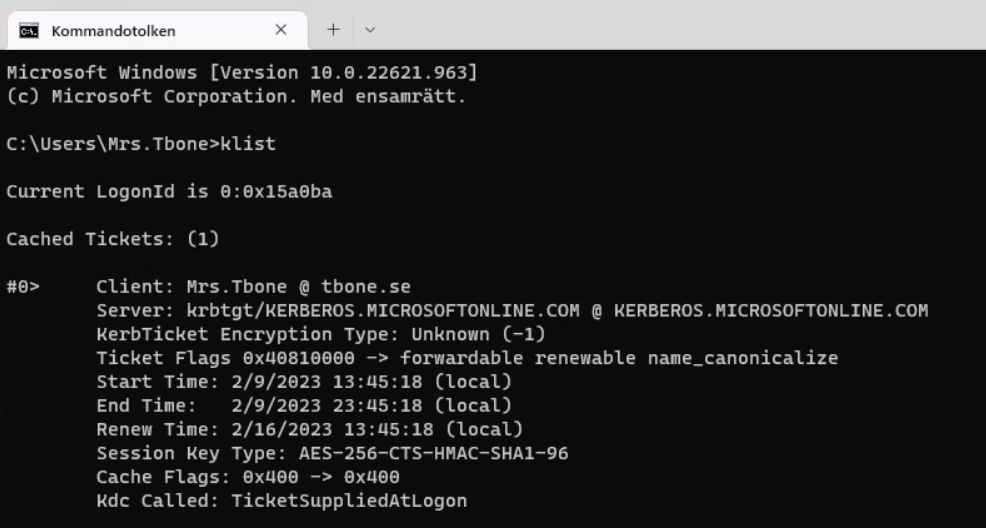
After a reboot and new login I run klist again in CMD. Now the Kerberos ticket is created and ready to give me access:
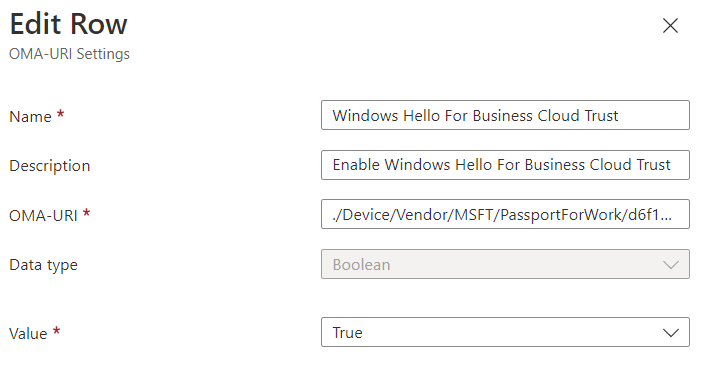
Extra Tip – Enable Windows Hello Cloud Trust for OnPrem Auth on Windows Device
When we enable Azure AD Kerberos and Cloud Trust for AAD joined machines, why not also enable Windows Hello to be able to use Azure Kerberos Cloud Trust for sign in and SSO. This also require an additional setting in Windows. Can be configured in the same custom configuration profile as above or create a new one.
- Open Intune Portal
- Select Devices / Windows / Configuration profiles
- Click Create Profile
- Platform: Windows 10 and later
- Profile type: Templates
- Template name: Custom
- Enter a suitable Name and Description and click Next
- On the Configuration settings, click Add
- Enter the following settings (replace TENANTID with your TenantID):
- Name: Use Cloud Trust For OnPrem Auth
- Description: Use Cloud Trust For OnPrem Auth
- OMA-URI: ./Device/Vendor/MSFT/PassportForWork/TENANTID/Policies/UseCloudTrustForOnPremAuth
- Data type: Boolean
- Value: True