Intune Cloud PKI and Entra CBA for Frontline Workers
In my last blog I described how to setup Intune Cloud PKI. That is quite simple. But how can we use it. How about implementing a Password-less solution for your frontline workers that are using only an Android device? When On-boarding, you hand out the username, Temporary access key and the Android device, then the user ca enroll and start working without ever knowing the password.
Why Password-less?
Password-less authentication is considered more secure than traditional passwords for several reasons:
- Reduction of User Error: Passwords can be weak, reused across multiple sites, or written down, making them vulnerable. Password-less systems often eliminate these risks.
- Phishing Resistance: Password-less authentication methods like one-time codes, special links, are typically used only once and are not vulnerable to typical phishing attacks that steal static passwords.
- Public Key Cryptography: Systems like passkeys use public key cryptography, where the private key needed to authenticate is never shared with the server, making it more secure against attacks.
- No Shared Secrets: With password-less authentication, there are no shared secrets like passwords that can be stolen or leaked from the server.
- Convenience: Password-less authentication can be more user-friendly, which encourages better security practices. Users are less likely to take shortcuts that compromise security when the process is easy and straightforward.
Overall, password-less authentication reduces the risk of compromised credentials and simplifies the login process, leading to a more secure and user-friendly experience.
Entra Certificate Based Authentication
Microsoft Entra Certificate-Based Authentication (CBA) is a method that allows users to authenticate using X.509 certificates instead of traditional passwords, providing a password-less experience.
Key Benefits:
- Great User Experience: Users can authenticate directly against Microsoft Entra ID without passwords.
- Great Admin Experience: No need for setting up any O-premise solutions like Active Directory Federation Services (AD FS).
- Easy to Deploy and Administer: It simplifies customer environments and reduces costs as it doesn’t require complex on-premises deployments.
- Secure: It doesn’t store on-premises passwords in the cloud and works with Microsoft Entra Conditional Access policies to provide phishing-resistant multifactor authentication (MFA).
Why CBA for Frontline workers on Android?
With a certificate stored in the Android device, the frontline worker do not need to know any password. When enrolling the phone, the frontline worker will set a PIN or biometric security on the device. That’s the only thing they need to remember. No more password changes, no more lost passwords. The PIN only works on that particular device and no where else. If the device is stolen, just wipe the device! Just like blocking an account but with a lot smaller attack surface.
How to Configure CBA with Intune Cloud PKI
Configure certification authorities in Microsoft Entra
- Open Intune Portal
- Open Tenant Administration
- Select Cloud PKI
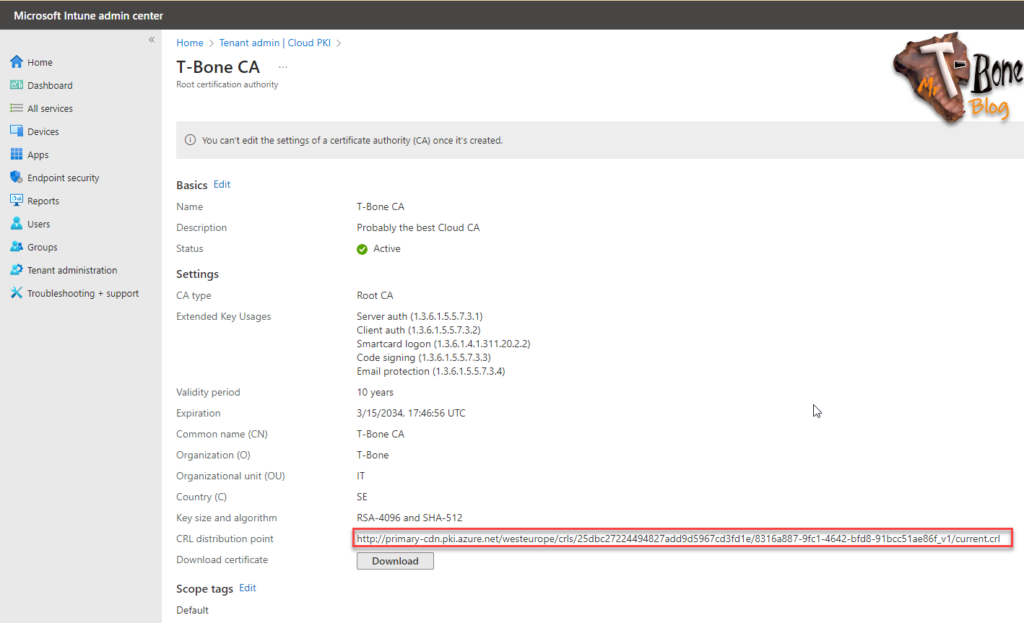
- Select and Open your Root CA Properties
- Click on Download to download the Root certificate
- Copy also the CRL distribution point URL
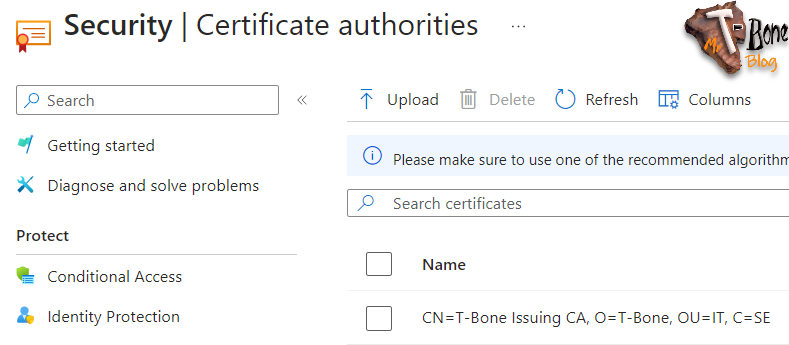
- Open Entra Portal
- Expand Protection
- Select Security Center
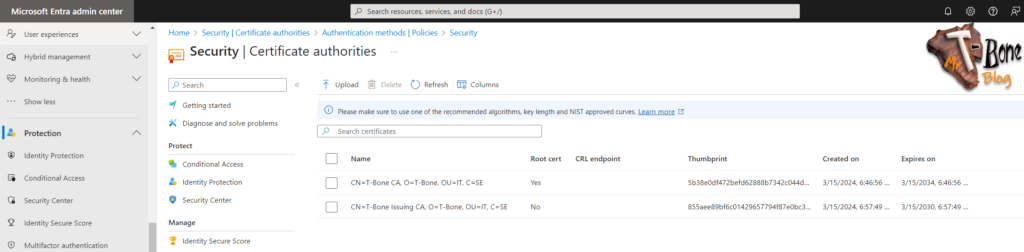
- Select Certificate authorities
- Click Upload to upload a certificate
- Add your Root certificate, select Yes on “Is root CA certificate”
- Paste your Certificate Revocation List URL and click Add
- Go back to Intune Portal
- Open Tenant Administration
- Select Cloud PKI
- Select and Open your Issuing CA Properties
- Click on Download to download the Issuing certificate
- Copy also the CRL distribution point URL
- Go back to Entra Portal
- Expand Protection
- Select Security Center
- Select Certificate authorities
- Click Upload to upload a certificate
- Add your Issuing certificate, select No on “Is root CA certificate”
- Paste your Certificate Revocation List URL and click Add
Configure CBA Authentication Method as Multifactor
- Open Entra Portal
- Expand Protection
- Select Authentication Methods
- Select Certificate-based authentication
- Add the target user group in Include to enable CBA
- Select the tab Configure
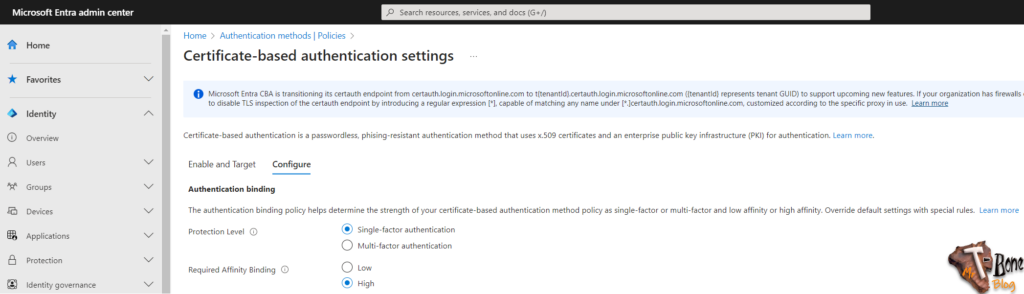
- Select if CBA by default, should be considered as Single– or Multi-factor authentication, I suggest Single and have an additional rule for your Cloud PKI.
- Select the Required Affinity Binding default setting to High
Low – Allow only a single text based mapping in certificate, like only userprincipalname
High – requires you to set a strong binding such as updating your user certificateUserIds field with the serial number of the certificate
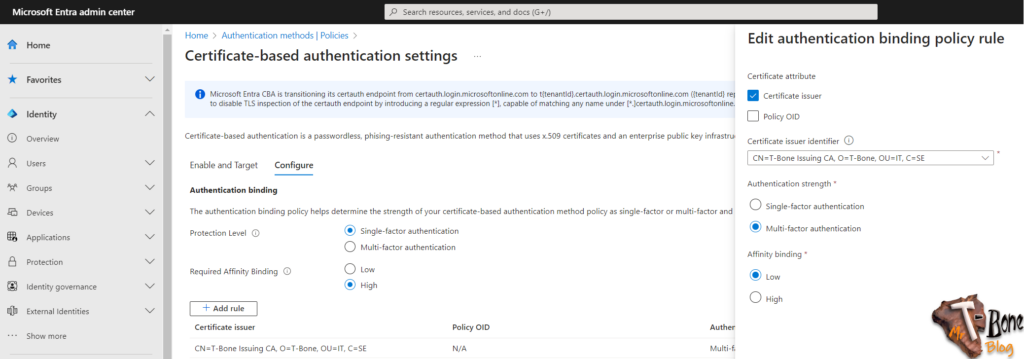
- Click on +Add Rule
- Check Certificate Issuer and select your Issuing CA
- Select Authentication Strength: Multi-factor authentication and Affinity binding: Low
(Right now the Cloud PKI does not enter certificate info in Entra ID, so we cannot use High)
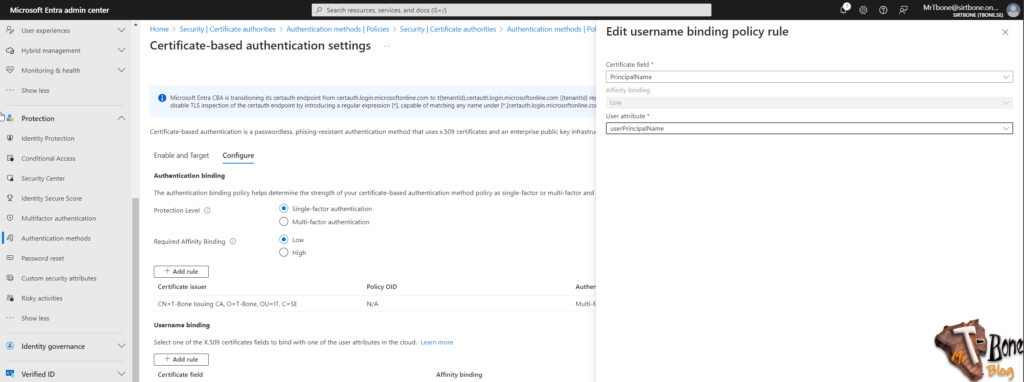
- Remove all Username Binding rules except PrinicipalName
- If PrincipalName is missing, Click +Add Rule
- Select Certificate Field: Principalname
- Select user attribute: UserPrincipalName
- Click Save
Deploy the User Certificate with Intune
- Open Intune Portal
- Open Devices
- Select Configuration
- Click + Create and New Policy
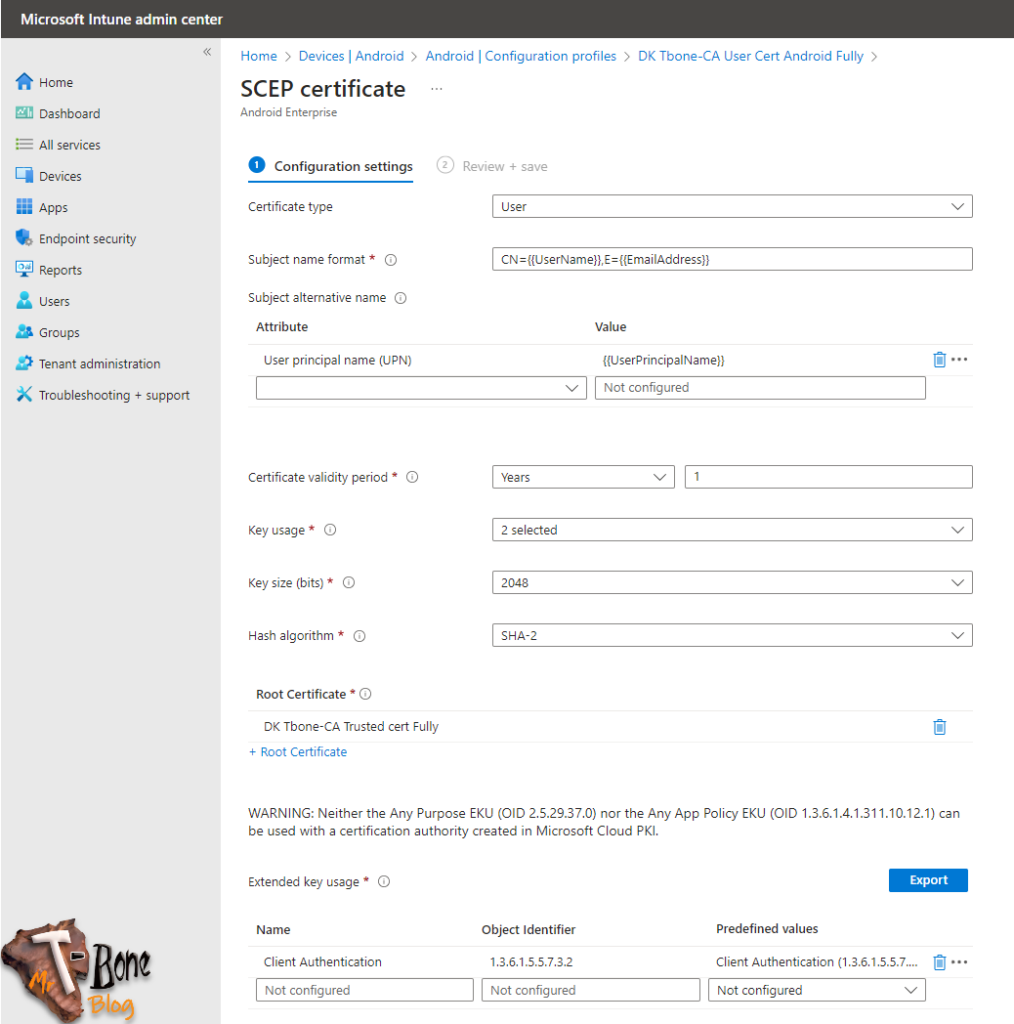
- Create a profile for Android Enterprise with the template SCEP certificate
Certificate Type: User
Subject Name Format: CN={{UserName}},E={{EmailAddress}}
Subject Alternative Name: User Principal Name = {{UserPrincipalName}}
Certificate Validity Period: 1 Years
Key Usage: Digital Signature, Key encipherment
Key size: 2048
Hash algorithm: SHA-2
Root Certificate authority: Select your deployed Trusted Root Certificate
Extended Key Usage: Client Authentication
Renewal threshold: 20
SCEP Server URL: Your SCEP server URL
On-Boarding Frontline Worker Password-less with TAP and CBA
A Temporary Access Pass (TAP) is a time-limited passcode used in Microsoft Entra to help users set up or recover password-less authentication methods. TAP is designed to assist in the onboarding of password-less authentication methods like FIDO2, Windows Hello for Business, CBA and the Microsoft Authenticator app. It’s also useful for account recovery when a user has lost their authentication device. Admins can enable TAP in the Microsoft Entra admin center, specifying settings such as the pass’s lifetime and which users can use i, just like with CBA. I will not go into details of that, so read more here.
Once a TAP is created, a user can sign in with it to register new password-less authentication methods or recover access to their account if they’ve lost their primary authentication factor. TAP enhances security by providing a way to register or recover passwordless methods without relying on a password, reducing the risk of password-related breaches.
- Create the new user.
- Add licenses to the user (Important to assign Intune and Intune Premium to get the certificate)
- Issue a TAP for the new user
- Deliver the Username, TAP and Android Device to the user.
- The user starts the On-Boarding, using his TAP to enroll the device, and then select a certificate to logon to all Microsoft 365 services.
This video show the end user experience when enrolling a Fully Managed Android Enterprise with QR code and TAP to finally get to password-less CBA!
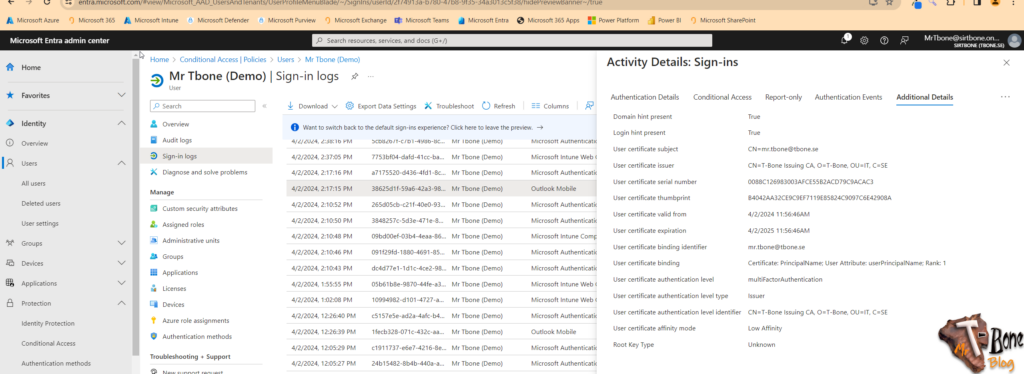
You can also verify and troubleshoot the CBA by using the Sign-in logs. Just open the tab Additional Details and you will see more info on the CBA authentication that was performed.
So start testing Intune PKI and CBA for your firstline workers!